Hey community! If you’re running an MCP (Model Context Protocol) server, you’ve already taken a step toward building smarter, context-aware systems that talk with AI models. But as with any server, security should never be an afterthought. In this post, we’ll go over — how to keep your MCP server safe.
1. Understand What You’re Protecting
An MCP server connects different “sources of truth” (like databases, APIs, or files) to an AI model.
That means your server might hold:
- User data
- API keys
- Internal business logic
- Sensitive prompts or context
So your main goal: make sure only the right people — and the right models — can access it.
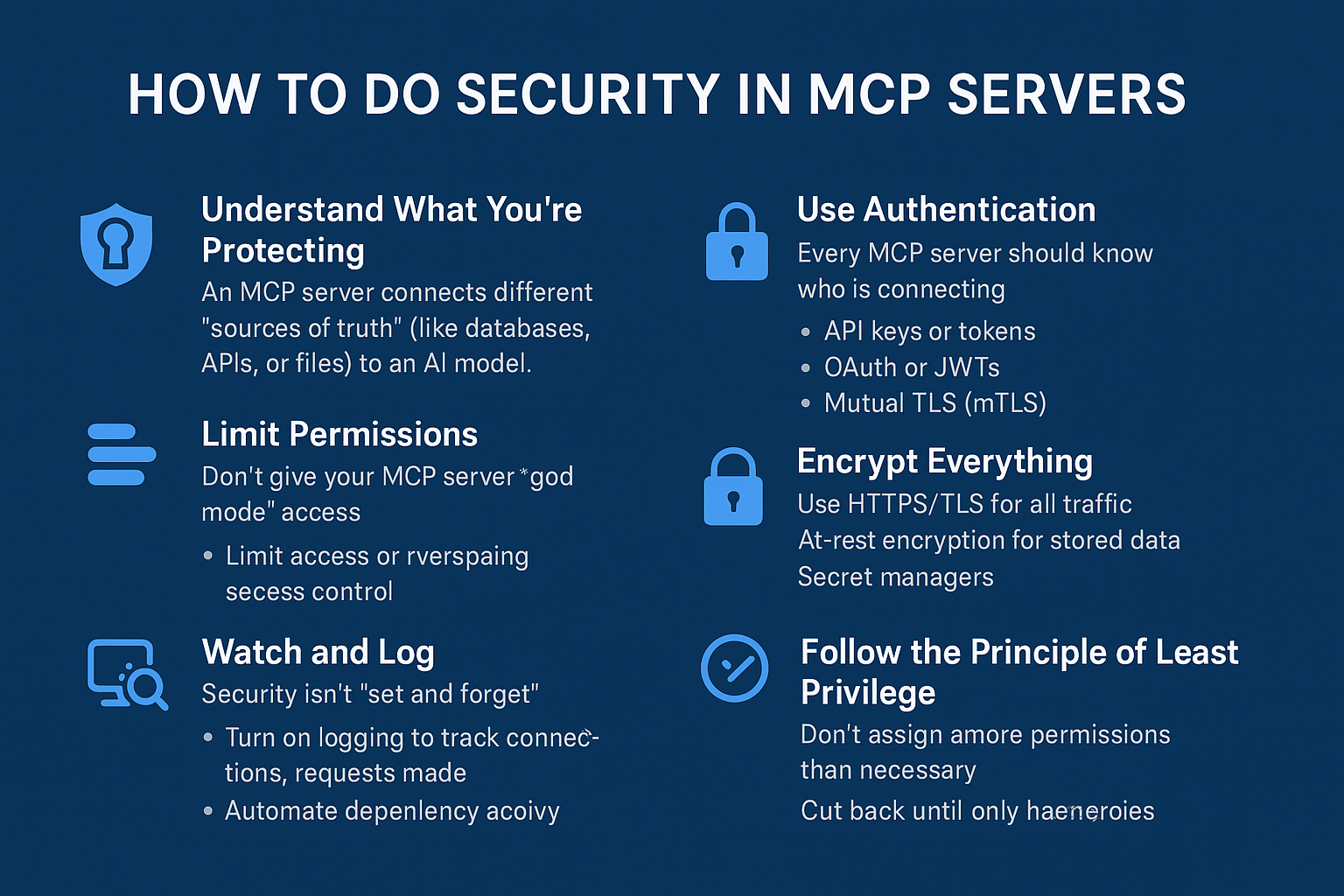
2. Use Authentication
Every MCP server should know who is connecting.
Start with:
- API keys or tokens: Give each client a unique token. Rotate these keys often.
- OAuth or JWTs: If you have users, use proper token-based login systems instead of passwords in plain text.
- Mutual TLS (mTLS): For more secure setups, both client and server verify each other with certificates.
Basically, never let an “open” MCP server sit on the internet without checking who’s knocking.
3. Limit Permissions
Don’t give your MCP server “god mode” access.
Set clear limits:
- Only allow access to the data or tools needed.
- Use role-based access control (RBAC) if you have multiple clients.
- Never expose raw system commands or sensitive files.
Think of it like giving your guests keys to one room, not your whole house.
4. Encrypt Everything
Even if someone intercepts your traffic, encryption makes it unreadable.
Use:
- HTTPS/TLS for all traffic
- At-rest encryption for stored data (like logs or configs)
- Secret managers (like Vault, AWS Secrets Manager, or environment variables) to store API keys
Never hardcode secrets into your MCP code.
5. Watch and Log
Security isn’t “set and forget.”
Turn on logging so you can:
- Track who connected
- See what requests were made
- Catch weird or unexpected activity
Use monitoring tools or alerts to spot unusual patterns (like lots of failed auth attempts).
6. Keep It Updated
Security holes pop up all the time — especially in dependencies.
- Keep your MCP server and its libraries updated
- Patch vulnerabilities as soon as possible
- Automate dependency checks if you can
It’s boring but vital — old code is the hacker’s best friend.
7. Test Your Setup
Try to break your own security before someone else does.
- Run basic penetration tests or use tools like OWASP ZAP
- Simulate expired tokens or unauthorized access
- Make sure errors don’t leak sensitive info (like stack traces or secrets)
8. Follow the Principle of Least Privilege
Always ask: “Does this part really need that permission?”
Cut back until it only has what’s needed to do its job — nothing more.
Summary
Here’s the short version:
| Step |
What to Do |
| 1 |
Know what you’re protecting |
| 2 |
Add authentication |
| 3 |
Limit permissions |
| 4 |
Encrypt data |
| 5 |
Log and monitor |
| 6 |
Keep it updated |
| 7 |
Test your security |
| 8 |
Use least privilege |
Final Thoughts
Good security isn’t about making your MCP server bulletproof — it’s about making it harder for bad actors and easier for you to catch issues early. Start small. Lock the front door (authentication), close unused windows (permissions), and keep your software clean (updates). Do that, and you’re already ahead of most. Thanks for reading! More awesome blogs are on the way with SightSpeak AI, so stay tuned for what’s next!